Linux SSH Key + Password Auth for Users Stored in Active Directory
In this blog we setup SSH with key and password authentication to achieve a 2FA type mechanism for more security for users stored in Active Directory. The SSH public key and the password of the user will be stored in the active directory as well.
OS used: CentOS 7 and Windows Server 2019.
Create User and Add to Group
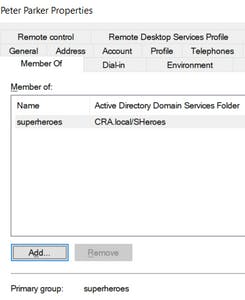
We have created a normal user in Active Directory named Peter Parker with username as ‘pparker’ and also have created a group named ‘superheroes’

We make pparker a member of the group superheroes and set the group as primary. We are creating a group so that we can also include the case of setting specific SSH settings to a particular set of users.
Connect Linux machine to AD using SSSD
We will now join our Linux machine to our existing Domain ‘CRA.local’
First we install sssd by running the following commands.
# yum install sssd realmd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools krb5-workstation openldap-clients policycoreutils-python
We add the IP and hostname of our AD server i.e Domain Controller in the /etc/hosts and /etc/resolv.conf file so that our machine can easily resolve the hostname of our AD server.
The hostname of the AD server is CRA-DC which can be seen here
in /etc/hosts file
192.168.40.139 CRA-DC.CRA.local CRA-DC
In /etc/resolv.conf
search CRA.local
nameserver 192.168.40.139
We now join our linux machine to the domain using the realm command. Make sure the linux machine doesn’t have hostname ‘localhost’ because it will cause an error.
# realm join --user=Administrator CRA-DC.CRA.local
We can verify whether our linux machine has joined the domain or not by running this command
# realm list
It should look something like this.
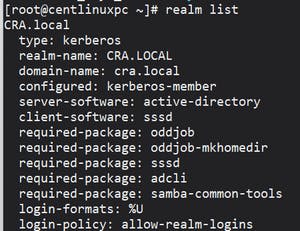
We have login-formats: %U because I have edited the /etc/sssd/sssd.conf file and set the values as
use_fully_qualified_names = False
Make sure to restart the service using
# systemctl restart sssd
We can check if we can fetch our user pparker using the id command
# id pparker
uid=1490001106(pparker) gid=1490001601(sftpusers1) groups=1490001601(sftpusers1),1490001603(superheroes)
As configured in the AD server before, we can find our user and the group it belongs to. Yay !
Generating and Adding SSH keys to AD
Here I have generated ssh keys using the ssh-keygen. As SSH on linux supports OpenSSH its required that we generate the keys in the required format.
To generate keys we can run this command on Linux as well as windows
ssh-keygen -t rsa -f pparkerkeys
We get the public and private keys
The private keys will be stored by the user authenticating and the public key will be stored in the AD
Storing the public key of pparker in the AD
- We can store the SSH public key in the AltSecurityIdentities attribute of the user.
- Server Manager > Tools > Active Directory Users and Computers > View and click on Advanced Features
- Then open the attributes of the user pparker and click on Attribute Editor
- Find the AltSecurityIdentities attribute and set the value as the value of the SSH public key that we just generated.
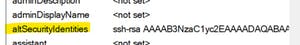
5. The key should generally be in the format:
ssh-rsa key_something_value user@hostname (this format worked for me)
Making Changes in SSSD and SSHd config
To retrieve and use the keys present in the AD. We will need to make few changes to the sssd config fille
Edit the /etc/sssd/sssd.conf file:
In the [domain/domain_name]
ldap_user_extra_attrs = altSecurityIdentities:altSecurityIdentities
ldap_user_ssh_public_key = altSecurityIdentities
ldap_use_tokengroups = True
In the [sssd] section
services = nss, pam, sudo, ssh
In the /etc/ssh/sshd_config :
Match Group superheroes
AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys
AuthorizedKeysCommandUser root
AuthenticationMethods "publickey,password"
- The Match Group superheroes(optional). Here I want to apply these config lines to the users that belong to the group superheroes that we had created in our AD.
- 2nd and 3rd line leads causes the keys and passwords to be fetched from the AD
- 4th line: It enables public key and password authentication. If either one is missing during login it wont allow (optional line for more security)
Suggested to select the lines as per your needs.
Restart both services
# systemctl restart sssd
# systemctl restart sshd
And now we are able to login using the private keys and password for the user pparker which is stored in the AD. Yas !
References :
This blog reposted from my personal website.